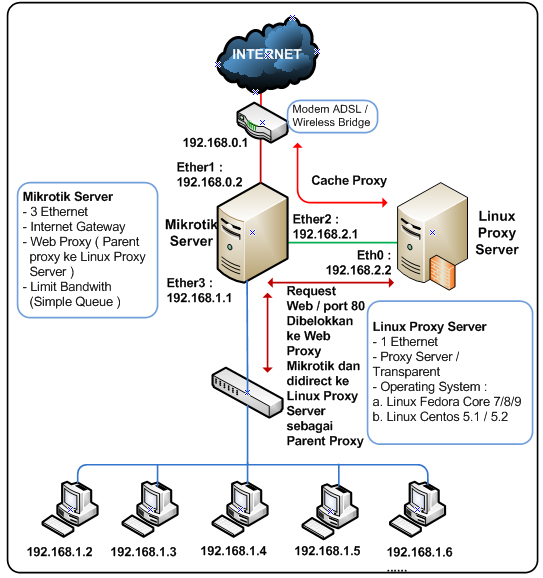
Skema Mikrotik
1. Brute Force Filter
/ip firewall filteradd chain=input protocol=tcp dst-port=22 src-address-list=ssh_blacklist action=drop comment=”Drop SSH brute forcers” disabled=noadd chain=input protocol=tcp dst-port=22 connection-state=new src-address-list=ssh_stage3 action=add-src-to-address-list address-list=ssh_blacklist \address-list-timeout=1w3d comment=”” disabled=noadd chain=input protocol=tcp dst-port=22 connection-state=new src-address-list=ssh_stage2 action=add-src-to-address-list address-list=ssh_stage3 \address-list-timeout=1m comment=”” disabled=noadd chain=input protocol=tcp dst-port=22 connection-state=new src-address-list=ssh_stage1 action=add-src-to-address-list address-list=ssh_stage2 \address-list-timeout=1m comment=”” disabled=noadd chain=input protocol=tcp dst-port=22 connection-state=new action=add-src-to-address-list address-list=ssh_stage1 address-list-timeout=1m comment=”” \disabled=no
2. Port Scanning Filter
/ip firewall filteradd chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w comment=”Port Scanners to list \” disabled=noadd chain=input protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w \comment=”” disabled=noadd chain=input protocol=tcp tcp-flags=fin,syn action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w comment=”” disabled=noadd chain=input protocol=tcp tcp-flags=syn,rst action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w comment=”” disabled=noadd chain=input protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w \comment=”” disabled=noadd chain=input protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w comment=”” \disabled=noadd chain=input protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg action=add-src-to-address-list address-list=”port scanners” address-list-timeout=2w \comment=”” disabled=noadd chain=input src-address-list=”port scanners” action=drop comment=”” disabled=no
3. FTP Port Filter
/ip firewall filteradd chain=input protocol=tcp dst-port=21 src-address-list=ftp_blacklist action=drop comment=”Filter FTP to Box” disabled=noadd chain=output protocol=tcp content=”530 Login incorrect” dst-limit=1/1m,9,dst-address/1m action=accept comment=”” disabled=noadd chain=output protocol=tcp content=”530 Login incorrect” action=add-dst-to-address-list address-list=ftp_blacklist address-list-timeout=3h comment=”” \disabled=no
4. Separate Packet Flag
/ip firewall filteradd chain=forward protocol=tcp action=jump jump-target=tcp comment=”Separate Protocol into Chains” disabled=noadd chain=forward protocol=udp action=jump jump-target=udp comment=”” disabled=noadd chain=forward protocol=icmp action=jump jump-target=icmp comment=”” disabled=no
5. Blocking UDP unknow trafict
/ip firewall filteradd chain=udp protocol=udp dst-port=69 action=drop comment=”Blocking UDP Packet” disabled=noadd chain=udp protocol=udp dst-port=111 action=drop comment=”” disabled=noadd chain=udp protocol=udp dst-port=135 action=drop comment=”” disabled=noadd chain=udp protocol=udp dst-port=137-139 action=drop comment=”” disabled=noadd chain=udp protocol=udp dst-port=2049 action=drop comment=”” disabled=noadd chain=udp protocol=udp dst-port=3133 action=drop comment=”” disabled=no
6. Blocking TCP unknow trafict
/ip firewall filteradd chain=tcp protocol=tcp dst-port=69 action=drop comment=”Bloking TCP Packet” disabled=noadd chain=tcp protocol=tcp dst-port=111 action=drop comment=”” disabled=noadd chain=tcp protocol=tcp dst-port=119 action=drop comment=”” disabled=noadd chain=tcp protocol=tcp dst-port=135 action=drop comment=”” disabled=noadd chain=tcp protocol=tcp dst-port=137-139 action=drop comment=”” disabled=noadd chain=tcp protocol=tcp dst-port=445 action=drop comment=”” disabled=noadd chain=tcp protocol=tcp dst-port=2049 action=drop comment=”” disabled=noadd chain=tcp protocol=tcp dst-port=12345-12346 action=drop comment=”” disabled=noadd chain=tcp protocol=tcp dst-port=20034 action=drop comment=”” disabled=noadd chain=tcp protocol=tcp dst-port=3133 action=drop comment=”” disabled=noadd chain=tcp protocol=tcp dst-port=67-68 action=drop comment=”” disabled=no
7. Blocking Bulk mail trafict
/ip firewall filteradd chain=forward protocol=tcp dst-port=25 action=drop comment=”Allow SMTP” disabled=no
8. DDoS Filter
/ip firewall filteradd chain=icmp protocol=icmp icmp-options=0:0-255 limit=5,5 action=accept comment=”Limited Ping Flood” disabled=noadd chain=icmp protocol=icmp icmp-options=3:3 limit=5,5 action=accept comment=”” disabled=noadd chain=icmp protocol=icmp icmp-options=3:4 limit=5,5 action=accept comment=”” disabled=noadd chain=icmp protocol=icmp icmp-options=8:0-255 limit=5,5 action=accept comment=”” disabled=noadd chain=icmp protocol=icmp icmp-options=11:0-255 limit=5,5 action=accept comment=”” disabled=noadd chain=icmp protocol=icmp action=drop comment=”” disabled=no
9. Filter P2P Connection
/ip firewall filteradd chain=forward p2p=all-p2p action=accept comment=”trafik P2P ” disabled=no
10. Filter Mapping routing access
/ip firewall filteradd chain=input dst-address-type=broadcast,multicast action=accept comment=”Allow Broadcast Traffic” disabled=noadd chain=input src-address=192.168.0.0/28 action=accept comment=”Allow access to router from known network” disabled=noadd chain=input src-address=192.168.1.0/24 action=accept comment=”” disabled=noadd chain=input src-address=192.168.2.0/30 action=accept comment=”” disabled=noadd chain=input src-address=125.162.0.0/16 action=accept comment=”” disabled=no
11. Filter Junk Connection
/ip firewall filteradd chain=input connection-state=established action=accept comment=”Connection State” disabled=noadd chain=input connection-state=related action=accept comment=”” disabled=noadd chain=input connection-state=invalid action=drop comment=”” disabled=no
Untuk Script lengkapnya silahkan Download DISINI
Semoga bermanfaat…. ^__^
Sumber : ForumMikrotik
No comments:
Post a Comment