Showing posts with label Mikrotik. Show all posts
Showing posts with label Mikrotik. Show all posts
Tuesday, 15 January 2013
Script auto change dns + flush dns
Bikin script dulu dengan nama “proteksi” source code gini:
/ip dns cache flush
/ip dns set primary-dns=208.67.222.222
/ip dns set secondary-dns=208.67.220.220
dan satu lagi dengan nama “bebas”:
/ip dns cache flush
/ip dns set primary-dns=203.130.208.18
/ip dns set secondary-dns=202.134.1.10
Basic Firewall Mikrotik
Skema Mikrotik
Langkah sederhana setting firewall di mikrotik.
Mikrotik MRTG / Graphing
Graphing adalah tool pada mokrotik yang difungsikan untuk memantau perubahan parameter-parameter pada setiap waktu. Perubahan perubahan itu berupa grafik uptodate dan dapat diakses menggunakan browser.
Graphing dapat menampilkan informasi berupa:
* Resource usage (CPU, Memory and Disk usage)
* Traffic yang melewati interfaces
* Traffic yang melewati simple queues
Mengaktifkan fungsi graping
Klik menu Tool >Graphing>Resource Rules
Adalah mengaktifkan graphing untuk resource usage Mikrotik. Sedangkana allow address adalah IP mana saja yang boleh mengakses grafik tersebu,. 0.0.0.0/0 untuk semua ip address.
Saturday, 13 October 2012
Setting Optional-LoadBalance
Setting Optional-LoadBalance
Contoh 2 ISP load balance
interface ethernet set ether4 name=LAN
interface ethernet set ether3 name=WAN1
interface ethernet set ether2 name=WAN2
interface ethernet set ether1 name=WAN3
/ ip address
add address=10.1.0.1/27 network=10.1.0.0 broadcast=10.1.0.31 interface=LAN comment="LAN IP" disabled=no
add address=10.111.0.4/29 network=10.111.0.0 broadcast=10.111.0.7 interface=WAN1 comment="Fastnet A1/17" disabled=no
add address=10.112.0.2/29 network=10.112.0.0 broadcast=10.112.0.7 interface=WAN2 comment="Fastnet A1/1" disabled=no
ip dns set primary-dns=202.73.99.8 allow-remote-request=no
ip dns set secondary-dns=61.247.0.8 allow-remote-request=no
/ ip firewall mangle
add chain=prerouting in-interface=LAN connection-state=new nth=2,2 action=mark-connection new-connection-mark=odd passthrough=yes comment="" disabled=no
add chain=prerouting in-interface=LAN connection-mark=odd action=mark-routing new-routing-mark=odd passthrough=no comment="" disabled=no
add chain=prerouting in-interface=LAN connection-state=new nth=2,1 action=mark-connection new-connection-mark=even passthrough=yes comment="" disabled=no
add chain=prerouting in-interface=LAN connection-mark=even action=mark-routing new-routing-mark=even passthrough=no comment="" disabled=no
/ ip firewall nat
add chain=srcnat connection-mark=odd action=src-nat to-addresses=10.112.0.6 to-ports=0-65535 comment="" disabled=no
add chain=srcnat connection-mark=even action=src-nat to-addresses=10.111.0.6 to-ports=0-65535 comment="" disabled=no
/ ip route
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 routing-mark=odd comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 routing-mark=even comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 comment="" disabled=no
/ip pool add name=dhcp-pool ranges=192.168.0.31-192.168.0.100
/ip dhcp-server network add address=192.168.0.0/24 gateway=192.168.0.2
/ip dhcp-server add interface=LAN address-pool=dhcp-pool
interface ethernet set ether4 name=LAN
interface ethernet set ether3 name=WAN1
interface ethernet set ether2 name=WAN2
interface ethernet set ether1 name=WAN3
/ ip address
add address=10.1.0.1/27 network=10.1.0.0 broadcast=10.1.0.31 interface=LAN comment="LAN IP" disabled=no
add address=10.111.0.4/29 network=10.111.0.0 broadcast=10.111.0.7 interface=WAN1 comment="Fastnet A1/17" disabled=no
add address=10.112.0.2/29 network=10.112.0.0 broadcast=10.112.0.7 interface=WAN2 comment="Fastnet A1/1" disabled=no
ip dns set primary-dns=202.73.99.8 allow-remote-request=no
ip dns set secondary-dns=61.247.0.8 allow-remote-request=no
/ ip firewall mangle
add chain=prerouting in-interface=LAN connection-state=new nth=2,2 action=mark-connection new-connection-mark=odd passthrough=yes comment="" disabled=no
add chain=prerouting in-interface=LAN connection-mark=odd action=mark-routing new-routing-mark=odd passthrough=no comment="" disabled=no
add chain=prerouting in-interface=LAN connection-state=new nth=2,1 action=mark-connection new-connection-mark=even passthrough=yes comment="" disabled=no
add chain=prerouting in-interface=LAN connection-mark=even action=mark-routing new-routing-mark=even passthrough=no comment="" disabled=no
/ ip firewall nat
add chain=srcnat connection-mark=odd action=src-nat to-addresses=10.112.0.6 to-ports=0-65535 comment="" disabled=no
add chain=srcnat connection-mark=even action=src-nat to-addresses=10.111.0.6 to-ports=0-65535 comment="" disabled=no
/ ip route
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 routing-mark=odd comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 routing-mark=even comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 comment="" disabled=no
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 comment="" disabled=no
/ip pool add name=dhcp-pool ranges=192.168.0.31-192.168.0.100
/ip dhcp-server network add address=192.168.0.0/24 gateway=192.168.0.2
/ip dhcp-server add interface=LAN address-pool=dhcp-pool
Memblokir access isp ke router mikrotik
Memblokir access isp ke router mikrotik
Trik dari saya untuk memblokir access ISP anda
Assalamualaikum
maaf om-master semua, apabila penjelasan saya nanti kurang berkenan di hati...
begini ceritanya...
terlebih dahulu kita masukkan kabel ISP melalui Router Mikrotik, ini berguna untuk membuat semua access ISP dapat dikendalikan oleh kita sebagai client.
maka configurasi yang akan kita pakai sebagai berikut
ISP == Router (Mikrotik) == Firewall == Switch == Client
Nah dengan metode seperti inilah kita dapat membendung akses ISP ke jaringan private kita.
akan saya jelaskan 1 persatu rule nya :
rule pertama akan kita gunakan untuk menerima paket icmp dari isp ini berguna agar kita dapat mengakses layanan internet sebagaimana biasanya.
rule kedua seluruh input menuju router kita terima selama koneksi menuju router lancar atau established
Nah ini inti dari semua ini disini, seluruh akses isp yang menggunakan LAN Card 1 (ether1-gateway) akan di drop (ditolak), maka ISP tidak serta merta akan keluar masuk ke jaringan private kita sesuka hatinya, meski kita sebagai client internetnya.
untuk rule yang ketiga kita tetap akan menerima semua input dengan action=accept dengan catatan tetap terkoneksi di LAN router kita.
maaf apabila penjelasannya kurang berkenan.
sekian dari saya.
maaf om-master semua, apabila penjelasan saya nanti kurang berkenan di hati...
begini ceritanya...
terlebih dahulu kita masukkan kabel ISP melalui Router Mikrotik, ini berguna untuk membuat semua access ISP dapat dikendalikan oleh kita sebagai client.
maka configurasi yang akan kita pakai sebagai berikut
ISP == Router (Mikrotik) == Firewall == Switch == Client
Nah dengan metode seperti inilah kita dapat membendung akses ISP ke jaringan private kita.
akan saya jelaskan 1 persatu rule nya :
Code:
0 ;;; default configuration
chain=input action=accept protocol=icmprule pertama akan kita gunakan untuk menerima paket icmp dari isp ini berguna agar kita dapat mengakses layanan internet sebagaimana biasanya.
Code:
1 ;;; default configuration
chain=input action=accept connection-state=establishedrule kedua seluruh input menuju router kita terima selama koneksi menuju router lancar atau established
Code:
2 ;;; default configuration
chain=input action=drop in-interface=ether1-gatewayNah ini inti dari semua ini disini, seluruh akses isp yang menggunakan LAN Card 1 (ether1-gateway) akan di drop (ditolak), maka ISP tidak serta merta akan keluar masuk ke jaringan private kita sesuka hatinya, meski kita sebagai client internetnya.
Code:
3 ;;; default configuration
chain=input action=accept connection-state=related in-interface=ether1-gatewayuntuk rule yang ketiga kita tetap akan menerima semua input dengan action=accept dengan catatan tetap terkoneksi di LAN router kita.
maaf apabila penjelasannya kurang berkenan.
sekian dari saya.
Block Port Scanner di Mikrotik
Block Port Scanner di Mikrotik
Assalamu'alaikum...
di bagian filter:
Code:
/ip firewall filter
add chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w comment="Port scanners to list " disabled=no
Chain ini dipakai untuk mendaftar ip ke black-list address list
Chain selanjutnya untuk mendeteksi apakah ada indikasi aktifitas port scanner:
add chain=input protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="NMAP FIN Stealth scan"
add chain=input protocol=tcp tcp-flags=fin,syn
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="SYN/FIN scan"
add chain=input protocol=tcp tcp-flags=syn,rst
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="SYN/RST scan"
add chain=input protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="FIN/PSH/URG scan"
add chain=input protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="ALL/ALL scan"
add chain=input protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="NMAP NULL scan"
jika ada tanda tanda dari kejadian di atas, maka harus didrop scanning IPnya pakai perintah ini:
add chain=input src-address-list="port scanners" action=drop comment="dropping port scanners" disabled=no
sumber:
HTML Code:
http://wiki.mikrotik.com/wiki/Drop_port_scanners
di bagian filter:
Code:
/ip firewall filter
add chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list address-list="port scanners" address-list-timeout=2w comment="Port scanners to list " disabled=no
Chain ini dipakai untuk mendaftar ip ke black-list address list
Chain selanjutnya untuk mendeteksi apakah ada indikasi aktifitas port scanner:
add chain=input protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="NMAP FIN Stealth scan"
add chain=input protocol=tcp tcp-flags=fin,syn
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="SYN/FIN scan"
add chain=input protocol=tcp tcp-flags=syn,rst
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="SYN/RST scan"
add chain=input protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="FIN/PSH/URG scan"
add chain=input protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="ALL/ALL scan"
add chain=input protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="NMAP NULL scan"
jika ada tanda tanda dari kejadian di atas, maka harus didrop scanning IPnya pakai perintah ini:
add chain=input src-address-list="port scanners" action=drop comment="dropping port scanners" disabled=no
sumber:
HTML Code:
http://wiki.mikrotik.com/wiki/Drop_port_scanners
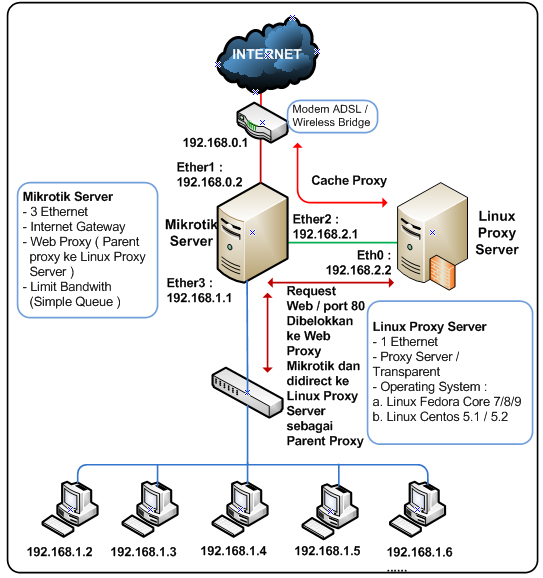
Redirect Mikrotik ke Squidbox linux
Redirect Mikrotik ke Squidbox linux
Assalamu'alaikum...
![[Image: pic-squidbox.jpg]](http://paidjo.files.wordpress.com/2008/03/pic-squidbox.jpg)
Banyak persoalan yg sering dialami pada web proxy di mikrotik, yaitu diantaranya tidak bisa di opreknya squid di mikrotik ini.
Disini saya akan mencoba berbagi ilmu, dan mohon koreksi bila ada yang salah. Ok..
![[Image: pic-squidbox.jpg]](http://paidjo.files.wordpress.com/2008/03/pic-squidbox.jpg)
Banyak persoalan yg sering dialami pada web proxy di mikrotik, yaitu diantaranya tidak bisa di opreknya squid di mikrotik ini.
Disini saya akan mencoba berbagi ilmu, dan mohon koreksi bila ada yang salah. Ok..
Firewall di mikrotik Full
Firewall di mikrotik Full
Assalamu'alaikum..
Dan sudah ada yang pernah di bahas di http://www.forummikrotik.com/
nah langsung saja, kita simak dengan seksama setting optimalisasi pada firewall di mikrotik.
Drop port scanners
Dan sudah ada yang pernah di bahas di http://www.forummikrotik.com/
nah langsung saja, kita simak dengan seksama setting optimalisasi pada firewall di mikrotik.
Drop port scanners
Code:
/ip firewall filter
add chain=input protocol=tcp psd=21,3s,3,1 action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="Port scanners to list " disabled=no
add chain=input protocol=tcp tcp-flags=fin,!syn,!rst,!psh,!ack,!urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="NMAP FIN Stealth scan"
add chain=input protocol=tcp tcp-flags=fin,syn
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="SYN/FIN scan"
add chain=input protocol=tcp tcp-flags=syn,rst
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="SYN/RST scan"
add chain=input protocol=tcp tcp-flags=fin,psh,urg,!syn,!rst,!ack
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="FIN/PSH/URG scan"
add chain=input protocol=tcp tcp-flags=fin,syn,rst,psh,ack,urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="ALL/ALL scan"
add chain=input protocol=tcp tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg
action=add-src-to-address-list address-list="port scanners"
address-list-timeout=2w comment="NMAP NULL scan"
add chain=input src-address-list="port scanners" action=drop comment="dropping port scanners" disabled=nofirewall anti virus di mikrotik
firewall anti virus di mikrotik
Assalamu'alaikum...
pada bagian ini ijinkan saya share tentang firewall filtering virus, sebelumnya hal ini sudah sering dibahas pada forum2 networking, terutama yaitu forum mikrotik indonesia,
okelah langsung saja, script ini tinggal copas aja, menggunakan new terminal.
pada bagian ini ijinkan saya share tentang firewall filtering virus, sebelumnya hal ini sudah sering dibahas pada forum2 networking, terutama yaitu forum mikrotik indonesia,
okelah langsung saja, script ini tinggal copas aja, menggunakan new terminal.
Subscribe to:
Posts (Atom)